When comparing motherboards for a new PC build or upgrade, understanding the security features is crucial. Among these, Secure Boot stands out as a fundamental aspect of modern system security. Let’s delve into what Secure Boot is and why it matters when you compare motherboards.
Quoting Particle.io:
…Secure Boot refers to the process of authenticating a device’s firmware and operating system against a known secure cryptographic key placed on the device at the time of manufacture. This authentication occurs every time the device is booted to validate that the firmware or code being loaded is the legitimate version that was placed there by whoever produced it.
This definition, initially for IoT devices, perfectly applies to PC motherboards as well. Think of your PC as a “thing” in the Internet of Things context. Whether you’re comparing a motherboard from 2012 or the latest model, the core principle of Secure Boot remains consistent: ensuring that only trusted and authorized software runs during the startup process.
To understand how Secure Boot impacts your motherboard choice, let’s break down the key steps and considerations.
Key Aspects of Secure Boot in Motherboards
To fully grasp Secure Boot when you compare motherboards, consider these detailed steps which outline how it functions within the motherboard’s firmware:
-
Understanding the Secure Boot Process: It’s essential to understand how Secure Boot operates within the motherboard’s UEFI firmware. This process, while complex, ensures a secure boot environment. Refer to resources like How Secure Boot works in Linux with regard to SuSE to visualize this flow. The foundational principles described in this 2012 article are still relevant to modern motherboard implementations of Secure Boot.
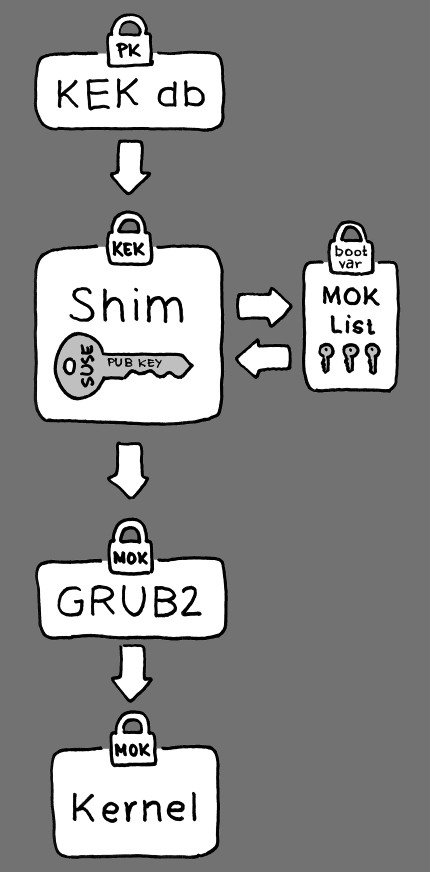 Flowchart for SecureBoot
Flowchart for SecureBoot -
Firmware Reset and Secure Boot Keys: When troubleshooting or reconfiguring Secure Boot, you might need to reset your motherboard’s firmware settings to factory defaults. This often involves actions like a PRAM reset on Macs, as outlined in guides like performing a PRAM Reset. Understanding how to manage and potentially reset the firmware keys is important when comparing motherboards, especially if you plan to customize your boot process.
-
Boot Manager and Key Enrollment: Modern systems often use boot managers like rEFInd to handle the boot process, especially when dual-booting operating systems. Tools and guides like those provided by Roderick Smith (outlined by Roderick Smith) explain how to install and configure such boot managers in conjunction with Secure Boot. The ability to enroll your own keys, as described in step 4, provides flexibility in managing Secure Boot on your motherboard.
-
MOK (Machine Owner Keys) Database: Enrolling keys into the MOK database allows you to extend the trust of Secure Boot to components like boot loaders and operating systems that might not be signed by the original equipment manufacturer. This step is crucial if you are installing custom operating systems or boot loaders and need to ensure they are trusted by the Secure Boot process. When you compare motherboards, consider the ease and flexibility they offer in managing Secure Boot keys and the MOK database.
-
Shim and Bootloader Interaction: The
shimis a small, signed bootloader that is often used to bridge the gap between the motherboard’s Secure Boot firmware and the actual operating system bootloader (like Grub2). Theshimis designed to be trusted by Secure Boot and, in turn, trusts other bootloaders after verifying their signatures. Understanding this chain of trust is important for diagnosing boot issues related to Secure Boot and for ensuring compatibility when comparing motherboards with different operating systems.
Troubleshooting Secure Boot Issues on Motherboards
If you encounter issues related to Secure Boot after comparing and choosing a motherboard, or when configuring your system, consider these troubleshooting steps. These are particularly relevant if the standard Secure Boot configuration is causing conflicts with your desired setup.
Referencing the Troubleshooting Section of Install openSUSE on a Mac can provide general guidance, even if you are not installing OpenSUSE on a Mac. A key insight, again from Roderick Smith, addresses potential firmware limitations:
Some EFI implementations (mostly from before 2014) do a poor job of honoring the boot options set via Linux’s efibootmgr or other tools. You may also lack access to such utilities, such as if you must install rEFInd in Windows. In such cases, you may need to change the boot loader’s name so that the EFI will see it as the default boot loader. rEFInd should then boot when your NVRAM lacks information on specific boot loaders to use.
This suggests that in some cases, especially with older motherboard firmware, you might need to adjust bootloader filenames to ensure they are recognized as default boot options. Renaming OpenSUSE’s shim<arch>.efi</arch> file to boot<arch>.efi</arch> and placing it in the BOOT directory (or root if no BOOT directory exists) might resolve boot issues if your motherboard firmware is limited to booting from a single default file. See Alternate Naming Options for more details on this naming convention.
These types of workarounds are sometimes necessary even on newer systems, as highlighted in discussions like Update NVRAM so that shimx64.efi is run instead of grubx64.efi on Debian system for secure boot. Understanding these potential firmware quirks is valuable when you compare motherboards, especially if you plan to use operating systems or configurations that might require Secure Boot adjustments.
Conclusion: Secure Boot and Motherboard Selection
When you compare motherboards, considering Secure Boot features is essential for modern PC security. While it operates behind the scenes, understanding its principles and potential troubleshooting steps is vital for a smooth and secure computing experience. By being informed about Secure Boot, you can make a more educated decision when selecting a motherboard that meets your security needs and compatibility requirements. This knowledge empowers you to navigate potential boot issues and ensures your system starts up in a secure and trusted state.
