Bcrypt is a widely used password-hashing function, but How Does Bcrypt Compare Work to secure your sensitive data? At COMPARE.EDU.VN, we’ll explore the inner workings of bcrypt, contrasting it with other hashing algorithms and highlighting its unique features that make it a robust security solution. By understanding bcrypt’s mechanisms, you can make informed decisions about your password security strategy, bolstering your defenses against potential threats and safeguard your valuable assets through strong encryption and key derivation techniques.
1. What Is Bcrypt and How Does It Differ From Other Hashing Algorithms?
Bcrypt is a key derivation function used for password hashing. Unlike faster hashing algorithms like SHA256 or MD5, bcrypt is deliberately slow to make brute-force attacks more difficult. It achieves this by incorporating a salt and an adaptive work factor, also known as cost factor, making it a more secure option for password storage than faster, unsalted hashing methods.
To further understand how bcrypt differs, let’s dive deeper into its key components and how they contribute to its overall security:
- Salt: Bcrypt always uses a salt, a random string added to the password before hashing. This ensures that even if two users have the same password, their hashes will be different, thwarting rainbow table attacks.
- Work Factor (Cost Factor): This parameter controls the number of iterations the bcrypt algorithm performs. Increasing the work factor exponentially increases the time it takes to compute the hash, making brute-force attacks significantly slower. This is adaptable, scaling with computing power.
- Key Derivation Function: Bcrypt is specifically designed as a key derivation function, optimized for password hashing. This contrasts with general-purpose hashing algorithms that are designed for speed and efficiency, not necessarily for security against brute-force attacks.
- Blowfish Cipher: Bcrypt is based on the Blowfish cipher, which has a slow key setup phase. This inherent slowness is leveraged to make bcrypt more resistant to attacks.
Compared to algorithms like SHA-256, which are designed for speed, bcrypt’s deliberate slowness is a key security feature. SHA-256 produces a fixed-size output, while bcrypt’s output includes the salt and iteration count, making it self-contained for verification.
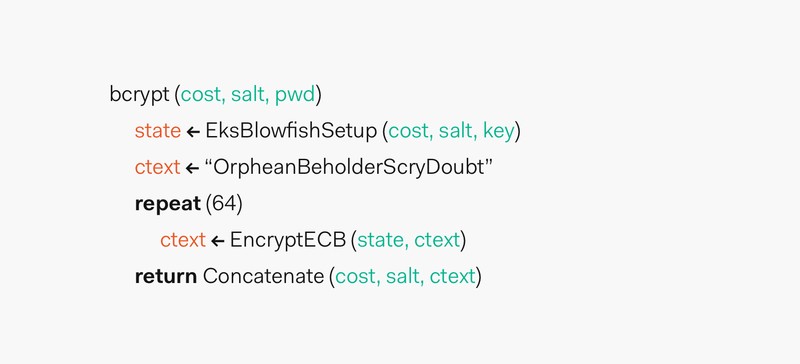 Diagram illustrating the bcrypt hashing process with salt and work factor
Diagram illustrating the bcrypt hashing process with salt and work factor
2. What Are the Key Features of Bcrypt That Enhance Password Security?
Bcrypt’s key features, including salting, adaptive work factor, and its Blowfish-based design, provide strong protection against various password attacks. These features contribute to its robustness and make it a preferred choice for secure password storage.
- Automatic Salting: Bcrypt automatically generates a unique salt for each password, preventing rainbow table attacks, where precomputed hashes are used to crack passwords quickly.
- Adaptive Work Factor: The work factor (or cost) can be adjusted to increase the computational effort required to hash a password. This allows bcrypt to scale with increasing computing power, ensuring that it remains secure against brute-force attacks in the future.
- Blowfish Cipher Foundation: Bcrypt is based on the Blowfish cipher, which has a slow key setup phase. This inherent slowness makes bcrypt more resistant to attacks compared to faster hashing algorithms.
- Preimage Resistance: It is computationally infeasible to reverse the hashing process and obtain the original password from the hash.
- Collision Resistance: It is computationally infeasible to find two different passwords that produce the same hash value.
These features combine to make bcrypt a highly secure password-hashing algorithm. The automatic salting and adaptive work factor, in particular, are crucial for maintaining security in the face of evolving threats and increasing computing power.
3. How Does Bcrypt’s Adaptive Work Factor Protect Against Brute-Force Attacks?
Bcrypt’s adaptive work factor, also known as the cost factor, is a critical mechanism for protecting against brute-force attacks. It allows you to increase the computational effort required to hash a password, making it exponentially more difficult for attackers to crack passwords by trying numerous combinations.
The work factor determines the number of iterations performed during the hashing process. Each increase in the work factor doubles the computation time. This means that even a small increase in the work factor can have a significant impact on the time it takes to crack a password.
For example, if a work factor of 10 takes 100 milliseconds to hash a password, a work factor of 11 will take approximately 200 milliseconds, and a work factor of 12 will take approximately 400 milliseconds. This exponential increase in computation time makes brute-force attacks much less feasible.
Attackers using powerful hardware or GPUs to crack passwords will find that bcrypt’s adaptive work factor significantly slows down their efforts. By adjusting the work factor, you can ensure that the time required to crack a password remains prohibitively long, even as computing power increases over time.
4. What Is Salting in Bcrypt and Why Is It Important for Security?
Salting in bcrypt involves adding a unique, random string to each password before it is hashed. This process is crucial for preventing rainbow table attacks and enhancing overall password security.
A rainbow table is a precomputed table of hashes that attackers can use to quickly crack passwords if they know the hashing algorithm and the passwords are not salted. By adding a unique salt to each password, the resulting hash is different even for identical passwords, rendering rainbow tables useless.
Here’s why salting is so important:
- Prevents Rainbow Table Attacks: Salts ensure that each password produces a unique hash, preventing attackers from using precomputed rainbow tables to crack multiple passwords at once.
- Mitigates Dictionary Attacks: Even if an attacker knows common passwords and their hashes, the unique salt makes each hash different, making dictionary attacks less effective.
- Enhances Overall Security: Salting adds an extra layer of security to the hashing process, making it more difficult for attackers to compromise passwords.
Bcrypt automatically handles salting, generating a unique salt for each password by default. This eliminates the need for developers to implement salting manually, reducing the risk of errors and ensuring that passwords are always securely salted.
5. How Does Bcrypt Compare To PBKDF2 and Argon2 For Password Hashing?
Bcrypt, PBKDF2, and Argon2 are all key derivation functions used for password hashing, but they differ in their design and security properties.
- Bcrypt: Based on the Blowfish cipher, bcrypt is deliberately slow and includes automatic salting and an adaptive work factor. It is widely used and considered a strong choice for password hashing.
- PBKDF2 (Password-Based Key Derivation Function 2): PBKDF2 can use various hashing algorithms (e.g., SHA-256) and applies a pseudorandom function to the password along with a salt. The iteration count determines the computational cost. PBKDF2 is flexible but may require more careful configuration than bcrypt to achieve comparable security levels.
- Argon2: Argon2 is a more recent key derivation function that won the Password Hashing Competition. It is designed to resist both GPU-based and memory-hard attacks. Argon2 has different variants (Argon2d, Argon2i, Argon2id) to suit different security needs.
Here’s a comparison table:
| Feature | Bcrypt | PBKDF2 | Argon2 |
|---|---|---|---|
| Underlying Algorithm | Blowfish cipher | Pseudorandom function (e.g., HMAC-SHA256) | Argon2-specific algorithm |
| Salting | Automatic | Requires manual implementation | Requires manual implementation |
| Adaptive Work Factor | Yes | Iteration count | Memory cost, time cost, parallelism |
| Resistance to GPU Attacks | Moderate | Moderate | High |
| Resistance to Memory-Hard Attacks | Low | Low | High |
| Complexity | Simple to use | More configuration required | More configuration required |
| Current Usage | Widespread | Common | Growing |
Argon2 is generally considered the most secure option due to its resistance to both GPU-based and memory-hard attacks. However, bcrypt remains a strong and widely used choice, especially when simplicity and ease of implementation are priorities. PBKDF2 can be secure if configured properly, but it requires more careful attention to parameters like the iteration count.
6. What Are the Recommended Work Factor (Cost) Settings for Bcrypt?
The recommended work factor (cost) setting for bcrypt depends on the hardware and the acceptable delay for user authentication. The goal is to choose a work factor that makes password hashing slow enough to deter attackers while maintaining a reasonable user experience.
OWASP (Open Web Application Security Project) recommends tuning the cost so that the hashing function takes approximately 1 second to run on your hardware. This provides a good balance between security and usability.
Here are some general guidelines:
- Minimum Work Factor: A work factor of 10 is often considered the minimum acceptable value.
- Modern Hardware: On modern hardware, a work factor of 12 or higher is recommended.
- Testing: Test different work factors on your hardware to determine the appropriate setting. Aim for a hashing time of around 1 second.
- Regular Updates: Re-evaluate the work factor periodically as hardware improves to maintain a consistent level of security.
It’s important to consider the user experience when setting the work factor. Users should not have to wait an excessive amount of time for authentication. However, a slight delay is acceptable if it significantly improves security.
7. How Can I Implement Bcrypt in My Web Application (Node.js Example)?
Implementing bcrypt in a web application involves integrating a bcrypt library into your backend code. Here’s an example of how to implement bcrypt in a Node.js application using the bcrypt library:
1. Install the bcrypt library:
npm install bcrypt2. Hash a password:
const bcrypt = require('bcrypt');
async function hashPassword(password) {
const saltRounds = 10; // Recommended: Adjust based on your hardware
const hashedPassword = await bcrypt.hash(password, saltRounds);
return hashedPassword;
}
// Example usage:
async function example() {
const password = 'MySecurePassword123';
const hashedPassword = await hashPassword(password);
console.log('Hashed password:', hashedPassword);
}
example();3. Verify a password:
const bcrypt = require('bcrypt');
async function verifyPassword(password, hashedPassword) {
const isMatch = await bcrypt.compare(password, hashedPassword);
return isMatch;
}
// Example usage:
async function example() {
const password = 'MySecurePassword123';
const hashedPassword = '$2b$10$EXAMPLE_HASH'; // Replace with your stored hash
const isMatch = await verifyPassword(password, hashedPassword);
console.log('Password matches:', isMatch);
}
example();Explanation:
bcrypt.hash(password, saltRounds): This function hashes the password using bcrypt with the specified number of salt rounds (work factor).bcrypt.compare(password, hashedPassword): This function compares the provided password with the stored hash. Bcrypt automatically extracts the salt from the hash and uses it to hash the provided password for comparison.
Remember to store the hashed password in your database and never store the plaintext password. When a user attempts to log in, compare the provided password with the stored hash using bcrypt.compare().
8. What Are the Common Pitfalls To Avoid When Using Bcrypt?
When using bcrypt, it’s essential to avoid common pitfalls that can compromise its security:
- Storing Plaintext Passwords: Never store plaintext passwords in your database. Always hash passwords before storing them.
- Using a Low Work Factor: Using a low work factor makes it easier for attackers to crack passwords. Choose a work factor that provides a good balance between security and usability.
- Not Salting Passwords: Bcrypt automatically salts passwords, but it’s crucial to ensure that salting is enabled and that each password has a unique salt.
- Using the Same Salt for All Passwords: Using the same salt for all passwords defeats the purpose of salting and makes rainbow table attacks possible.
- Not Updating the Work Factor: As hardware improves, it’s essential to re-evaluate and update the work factor to maintain a consistent level of security.
- Improper Error Handling: Handle errors properly to prevent information leakage and ensure that password hashing and verification processes are secure.
- Ignoring Security Best Practices: Always follow security best practices when implementing password hashing and storage. This includes using a strong password policy, implementing account lockout mechanisms, and regularly auditing your security practices.
By avoiding these pitfalls, you can ensure that bcrypt provides the strong password security it is designed to offer.
9. How Does Bcrypt Handle Password Reset and Recovery Processes?
Bcrypt, being a one-way hashing function, doesn’t allow for direct password recovery. Instead, password reset processes are typically used. Here’s how bcrypt is involved in these processes:
- Password Reset Request: The user initiates a password reset request, usually by providing their email address or username.
- Verification: The system verifies the user’s identity, often by sending a unique link or code to their email address.
- New Password: Once the user’s identity is verified, they are prompted to enter a new password.
- Hashing and Storage: The new password is then hashed using bcrypt with a new, randomly generated salt and stored in the database. The old hash is replaced with the new one.
During the password reset process, bcrypt ensures that the new password is securely hashed and stored. The old password, which is no longer needed, is effectively discarded and replaced with the new hash.
It’s important to note that password reset processes should be implemented securely to prevent unauthorized access. This includes using strong verification methods, generating unique and unpredictable reset links or codes, and implementing rate limiting to prevent brute-force attacks.
10. Where Can I Find More Resources and Information About Bcrypt Security Best Practices?
To further enhance your understanding of bcrypt and its security best practices, here are some valuable resources:
- OWASP (Open Web Application Security Project): The OWASP Password Storage Cheat Sheet provides comprehensive guidance on password storage best practices, including the use of bcrypt.
https://cheatsheetseries.owasp.org/cheatsheets/Password_Storage_Cheat_Sheet.html - Bcrypt Wikipedia Page: The Wikipedia page for bcrypt provides a detailed overview of the algorithm, its history, and its security properties.
https://en.wikipedia.org/wiki/Bcrypt - National Institute of Standards and Technology (NIST): NIST provides guidelines and standards for cryptography and security. While they may not have a specific document dedicated to bcrypt, their publications on password security and cryptography are valuable resources.
https://www.nist.gov/ - Security Blogs and Articles: Numerous security blogs and articles discuss bcrypt and its implementation. Search for reputable sources that provide in-depth analysis and practical advice.
- COMPARE.EDU.VN: Explore COMPARE.EDU.VN for more articles and comparisons on security technologies.
By consulting these resources, you can stay informed about the latest bcrypt security best practices and ensure that your password storage is as secure as possible.
Conclusion:
Bcrypt is a robust and widely used password-hashing algorithm that provides strong protection against various password attacks. Its key features, including automatic salting, adaptive work factor, and its Blowfish-based design, make it a preferred choice for secure password storage.
At COMPARE.EDU.VN, we understand the importance of making informed decisions about your security infrastructure. By providing in-depth comparisons and analysis, we aim to empower you to choose the best solutions for your needs.
Frequently Asked Questions (FAQ)
Q1: Is bcrypt still considered secure in 2024?
Yes, bcrypt is still considered a secure password-hashing algorithm in 2024, provided that it is implemented correctly and the work factor is set appropriately.
Q2: What is the difference between bcrypt and other hashing algorithms like SHA-256?
Bcrypt is deliberately slow and includes automatic salting and an adaptive work factor, making it more resistant to brute-force attacks compared to faster hashing algorithms like SHA-256.
Q3: How do I choose the right work factor for bcrypt?
The recommended work factor should be tuned so that the hashing function takes approximately 1 second to run on your hardware.
Q4: Does bcrypt automatically salt passwords?
Yes, bcrypt automatically generates a unique salt for each password by default.
Q5: What are the common mistakes to avoid when using bcrypt?
Common mistakes include storing plaintext passwords, using a low work factor, not salting passwords, and not updating the work factor as hardware improves.
Q6: Can I recover a password if it is hashed with bcrypt?
No, bcrypt is a one-way hashing function, so it is not possible to recover the original password from the hash. Password reset processes are typically used instead.
Q7: How does bcrypt protect against rainbow table attacks?
Bcrypt’s automatic salting ensures that each password produces a unique hash, preventing attackers from using precomputed rainbow tables to crack passwords.
Q8: Is bcrypt vulnerable to GPU-based attacks?
Bcrypt is somewhat vulnerable to GPU-based attacks, but its adaptive work factor can still make brute-force attacks computationally expensive. Argon2 is a more resistant alternative.
Q9: Where can I find the bcrypt library for my programming language?
Bcrypt libraries are available for many programming languages, including Node.js, Python, Java, and PHP. Search for reputable libraries on package managers like npm, PyPI, and Maven.
Q10: How often should I update the work factor for bcrypt?
Re-evaluate the work factor periodically (e.g., every 1-2 years) as hardware improves to maintain a consistent level of security.
Ready to make informed decisions? Visit COMPARE.EDU.VN for more insightful comparisons and detailed analyses.
Need more help?
Contact us at:
- Address: 333 Comparison Plaza, Choice City, CA 90210, United States
- Whatsapp: +1 (626) 555-9090
- Website: compare.edu.vn