Does Windows have a mechanism comparable to OpenSSL for verifying certificates, and how does it handle trusting root certificates downloaded from the AIA field? COMPARE.EDU.VN aims to clarify how Windows verifies certificates, particularly focusing on its approach to handling root certificates obtained from the Authority Information Access (AIA) field, offering alternatives like PowerShell and Certutil for detailed analysis and management, and similar utilities for different environments.
1. How Does Windows Verify Certificates Similar to OpenSSL?
Windows does indeed have its own built-in mechanisms for verifying certificates, though they operate differently from OpenSSL. While OpenSSL is a command-line tool often used in development and server environments, Windows integrates certificate verification directly into the operating system. This integration is leveraged by applications, browsers, and system services for secure communication and authentication.
1.1. Windows Certificate Stores
Windows maintains several certificate stores to manage trusted root certificates, intermediate certificates, and personal certificates. These stores are crucial for establishing trust during certificate verification. The primary stores include:
- Trusted Root Certification Authorities: Contains certificates of root CAs that Windows inherently trusts.
- Intermediate Certification Authorities: Holds certificates of intermediate CAs, which are used to build a chain of trust from an end-entity certificate to a trusted root.
- Personal: Stores certificates associated with the current user, often used for authentication and encryption.
- Trusted Publishers: Contains certificates of software publishers that are trusted to install software without prompting the user.
- Untrusted Certificates: Holds certificates that have been explicitly marked as untrusted.
These stores can be managed using the Microsoft Management Console (MMC) with the Certificates snap-in, or through PowerShell cmdlets.
1.2. Certificate Verification Process
When Windows encounters a certificate, it performs several checks to verify its validity and establish trust:
- Chain Building: Windows attempts to build a chain of trust from the end-entity certificate to a trusted root certificate. This involves examining the certificate’s issuer field and finding the corresponding issuer certificate in the appropriate certificate stores.
- Revocation Checking: Windows checks whether the certificate has been revoked by consulting Certificate Revocation Lists (CRLs) or Online Certificate Status Protocol (OCSP) responders. Revocation information is typically embedded in the certificate’s extensions.
- Signature Verification: Windows verifies the digital signature on the certificate to ensure that it has not been tampered with and that it was issued by the claimed issuer.
- Trust Evaluation: Windows evaluates the trust status of the root certificate in the chain. If the root certificate is present in the Trusted Root Certification Authorities store, the certificate is considered trusted.
If any of these checks fail, Windows will flag the certificate as invalid or untrusted.
1.3. Tools for Certificate Verification in Windows
Windows provides several tools for performing certificate verification tasks similar to OpenSSL. These tools offer different levels of functionality and are suitable for various scenarios:
- Certutil: A command-line utility that can be used to verify certificates, manage certificate stores, and perform other certificate-related tasks. It is a versatile tool for administrators and developers.
- PowerShell: Provides cmdlets for managing certificates and performing certificate verification. PowerShell is useful for automating certificate-related tasks and integrating certificate verification into scripts.
- Microsoft Management Console (MMC): With the Certificates snap-in, MMC allows users to view and manage certificates in a graphical interface. It is suitable for interactive certificate management.
1.4. Using Certutil for Certificate Verification
The certutil command-line utility is a powerful tool for verifying certificates in Windows. Here are some common use cases:
-
Verifying a Certificate:
certutil -verify -urlfetch test.exeThis command verifies the certificate of the
test.exefile, including checking the certificate chain and revocation status. The-urlfetchoption enables the tool to download missing certificates and revocation information from the URLs specified in the certificate. -
Displaying Certificate Information:
certutil -dump test.exeThis command displays detailed information about the certificate, including its serial number, issuer, subject, and extensions.
-
Managing Certificate Stores:
certutil -store <storename>This command allows you to view and manage the certificates in the specified certificate store.
1.5. Using PowerShell for Certificate Verification
PowerShell provides cmdlets for managing certificates and performing certificate verification. Here are some examples:
-
Getting Certificate Information:
$cert = Get-AuthenticodeSignature test.exe $cert.SignerCertificateThis script retrieves the certificate of the
test.exefile and displays its properties. -
Verifying Certificate Chain:
$cert = Get-AuthenticodeSignature test.exe $cert.SignerCertificate.Verify()This script verifies the certificate chain of the
test.exefile. -
Managing Certificate Stores:
Get-ChildItem Cert:CurrentUserMyThis command lists the certificates in the current user’s personal certificate store.
1.6. Comparison with OpenSSL
While Windows provides built-in tools for certificate verification, OpenSSL offers some advantages in certain scenarios:
- Cross-Platform Compatibility: OpenSSL is available on multiple operating systems, making it suitable for cross-platform development and deployment.
- Command-Line Interface: OpenSSL’s command-line interface is familiar to many developers and system administrators.
- Flexibility: OpenSSL provides a wide range of options and configurations for certificate verification.
However, Windows’ built-in tools offer tighter integration with the operating system and are often easier to use for basic certificate verification tasks.
1.7. Practical Examples
Consider a scenario where you need to verify the digital signature of an executable file downloaded from the internet. Using certutil, you can quickly verify the certificate and ensure that the file has not been tampered with. Similarly, PowerShell can be used to automate the verification process and integrate it into a script that checks the digital signatures of all executable files in a directory.
2. How Does Windows Handle Trusting Root Certificates Downloaded From the AIA Field?
The process by which Windows handles trusting root certificates downloaded from the AIA (Authority Information Access) field is a critical aspect of its certificate verification mechanism. The AIA field in a certificate specifies the URLs where information about the issuing CA can be found, including the CA’s certificate.
2.1. AIA Extension
The Authority Information Access (AIA) extension is a critical component of X.509 certificates, providing essential information about the certificate’s issuer. This extension includes URLs that point to the issuer’s certificate and other relevant data. It enables clients to automatically fetch necessary certificates to build a complete trust chain.
2.2. Automatic Root Certificate Download
When Windows encounters a certificate with an AIA extension, it can automatically download the issuer’s certificate from the specified URL if it is not already present in the system’s certificate stores. This feature is enabled by default but can be controlled through Group Policy settings.
2.3. Trust Considerations
The key question is: how does Windows decide whether to trust a root certificate that it has just downloaded from the AIA field? The answer lies in a combination of factors:
- Root Certificate Program: Windows participates in the Microsoft Root Certificate Program, which defines the criteria for CAs to be included in the Trusted Root Certification Authorities store. CAs that meet these criteria are included in the program, and their root certificates are distributed with Windows updates.
- Trust Lists: Windows uses trust lists to manage trusted root certificates. These lists are updated periodically through Windows Update and contain information about the CAs that are trusted by Microsoft.
- User Configuration: Users and administrators can configure the Trusted Root Certification Authorities store by adding or removing certificates. This allows them to customize the trust settings for their environment.
2.4. Steps in Trust Evaluation
When a root certificate is downloaded from the AIA field, Windows performs the following steps to evaluate its trust:
- Check for Presence in Trusted Root Store: Windows first checks whether the root certificate is already present in the Trusted Root Certification Authorities store. If it is, the certificate is considered trusted.
- Check for Presence in Trust Lists: If the root certificate is not in the Trusted Root store, Windows checks whether it is included in the Microsoft Root Certificate Program and present in the trust lists. If it is, the certificate is considered trusted.
- Evaluate Certificate Policies: Windows evaluates the certificate policies specified in the root certificate. These policies define the types of certificates that the CA is authorized to issue and the security requirements that must be met.
- User Prompts: In some cases, Windows may prompt the user to decide whether to trust the root certificate. This typically occurs when the certificate is not included in the Trusted Root store or the trust lists.
2.5. Group Policy Settings
Administrators can control the behavior of automatic root certificate downloads through Group Policy settings. These settings allow them to enable or disable automatic downloads, specify the URLs from which certificates can be downloaded, and configure other trust-related settings.
2.6. Potential Risks and Mitigation
While automatic root certificate downloads can simplify certificate verification, they also introduce potential risks:
- Compromised AIA Servers: If an AIA server is compromised, it could serve malicious certificates that could be used to bypass security checks.
- Rogue CAs: A rogue CA could issue certificates that are trusted by Windows, allowing them to impersonate legitimate websites or software publishers.
To mitigate these risks, it is important to:
- Monitor AIA Servers: Regularly monitor AIA servers for signs of compromise.
- Implement Certificate Pinning: Use certificate pinning to specify the expected certificates for specific websites or applications.
- Keep Windows Up-to-Date: Ensure that Windows is kept up-to-date with the latest security patches and trust list updates.
2.7. Examples of AIA in Action
Consider a scenario where a user visits a website that uses a certificate issued by an intermediate CA. If the user’s system does not have the intermediate CA certificate, Windows will automatically download it from the AIA URL specified in the website’s certificate. This allows Windows to build a complete chain of trust from the website’s certificate to a trusted root certificate, ensuring that the user can securely access the website.
2.8. Best Practices
To ensure the security and reliability of certificate verification in Windows, it is important to follow these best practices:
- Keep Certificate Stores Up-to-Date: Regularly update the Trusted Root Certification Authorities store and other certificate stores with the latest certificates and trust list updates.
- Monitor Certificate Usage: Monitor certificate usage to detect any suspicious activity.
- Implement Strong Certificate Policies: Implement strong certificate policies to ensure that certificates are issued and managed securely.
- Educate Users: Educate users about the risks associated with untrusted certificates and how to avoid them.
2.9. Importance of Revocation Checking
Certificate revocation checking is a crucial step in the certificate verification process. It ensures that certificates that have been compromised or are no longer valid are not trusted. Windows supports two mechanisms for certificate revocation checking:
- Certificate Revocation Lists (CRLs): CRLs are lists of revoked certificates that are published by CAs. Windows downloads CRLs from the URLs specified in the certificate’s CRL Distribution Points (CDP) extension.
- Online Certificate Status Protocol (OCSP): OCSP is a protocol that allows clients to query the revocation status of a certificate in real-time. Windows sends OCSP requests to OCSP responders specified in the certificate’s Authority Information Access (AIA) extension.
By performing revocation checking, Windows can ensure that certificates that have been revoked are not trusted, even if they were previously considered valid.
3. Alternatives to OpenSSL for Certificate Verification
While OpenSSL is a popular and powerful tool for certificate verification, several alternatives are available, each with its strengths and weaknesses. These alternatives cater to different environments and use cases, offering a range of features and functionalities.
3.1. Windows Certificate Tools
As discussed earlier, Windows provides built-in tools for certificate verification, including certutil and PowerShell cmdlets. These tools are tightly integrated with the operating system and are suitable for basic certificate verification tasks.
3.2. GnuTLS
GnuTLS is a free and open-source library that provides cryptographic functions, including certificate verification. It is similar to OpenSSL but is licensed under the GNU Lesser General Public License (LGPL), which may be more suitable for some projects.
GnuTLS supports various certificate formats, protocols, and cryptographic algorithms. It also includes command-line tools for certificate management and verification.
3.3. NSS (Network Security Services)
NSS is a set of libraries designed to support cross-platform development of security-enabled client and server applications. Developed by Mozilla, NSS is used in Firefox, Chrome, and other widely used software.
NSS provides APIs for performing cryptographic operations, including certificate verification. It supports various certificate formats, protocols, and cryptographic algorithms.
3.4. Bouncy Castle
Bouncy Castle is a collection of cryptographic APIs for Java and C#. It provides a wide range of cryptographic algorithms and protocols, including certificate verification.
Bouncy Castle is known for its comprehensive feature set and its support for emerging cryptographic standards. It is widely used in enterprise applications and security products.
3.5. Botan
Botan is a cryptographic library written in C++. It aims to provide a flexible and easy-to-use API while maintaining a high level of security and performance.
Botan supports various certificate formats, protocols, and cryptographic algorithms. It also includes features such as key management, random number generation, and hash functions.
3.6. Cryptography Libraries in Python
Python offers several libraries for performing cryptographic operations, including certificate verification. Some popular options include:
- cryptography: A package designed to expose cryptographic primitives and recipes to Python developers. It provides a high-level API for performing common cryptographic tasks, including certificate verification.
- pyOpenSSL: A Python wrapper around the OpenSSL library. It allows Python developers to access the full range of OpenSSL’s functionality, including certificate verification.
3.7. Comparison Table
| Feature | OpenSSL | Windows Certificate Tools | GnuTLS | NSS | Bouncy Castle | Botan | Python Cryptography Libraries |
|---|---|---|---|---|---|---|---|
| Operating Systems | Cross-platform | Windows | Cross-platform | Cross-platform | Java, C# | Cross-platform | Cross-platform |
| License | Apache | Proprietary | LGPL | MPL | MIT | BSD-like | Varies |
| Ease of Use | Moderate | Easy | Moderate | Moderate | Moderate | Moderate | Easy |
| Feature Set | Comprehensive | Basic | Comprehensive | Comprehensive | Comprehensive | Comprehensive | Moderate |
| Integration | Standalone | Tightly Integrated | Standalone | Standalone | Standalone | Standalone | Varies |
3.8. Choosing the Right Alternative
The choice of the right alternative to OpenSSL depends on the specific requirements of the project. Factors to consider include:
- Operating System: If the project is Windows-specific, the built-in Windows certificate tools may be the best option.
- Programming Language: If the project is written in Java or C#, Bouncy Castle may be a good choice. Python cryptography libraries are suitable for Python projects.
- License: The license of the library should be compatible with the project’s license.
- Feature Set: The library should provide the necessary cryptographic functions and protocols.
- Ease of Use: The library should be easy to use and integrate into the project.
By carefully considering these factors, developers can choose the alternative to OpenSSL that best meets their needs.
4. Comprehensive Guide to Troubleshooting Certificate Verification Issues
Certificate verification issues can be frustrating, whether you’re a developer, system administrator, or end-user. This section provides a comprehensive guide to troubleshooting common certificate verification problems, helping you identify the root cause and implement effective solutions.
4.1. Common Certificate Verification Errors
Before diving into troubleshooting, it’s essential to understand common certificate verification errors you might encounter:
- “The certificate is not trusted”: This error indicates that the certificate chain could not be validated to a trusted root CA.
- “The certificate has been revoked”: The certificate has been revoked by the issuing CA and should no longer be trusted.
- “The certificate has expired”: The certificate is no longer valid because its validity period has ended.
- “The certificate’s name does not match the site”: The domain name in the certificate does not match the domain name of the website being accessed.
- “The certificate chain is incomplete”: One or more intermediate certificates are missing from the certificate chain.
4.2. Initial Checks
When encountering a certificate verification error, start with these basic checks:
- Date and Time: Ensure that the system’s date and time are accurate. Incorrect date and time settings can cause certificate validity checks to fail.
- Network Connectivity: Verify that the system has a stable internet connection. Certificate revocation checks and AIA fetches require network access.
- Browser/Application Updates: Ensure that the browser or application being used is up-to-date. Updates often include fixes for certificate verification issues.
- Firewall/Proxy Settings: Check firewall and proxy settings to ensure that they are not blocking access to CRLs or OCSP responders.
4.3. Diagnosing Certificate Issues
If the initial checks don’t resolve the issue, proceed with more detailed diagnostics:
-
Examine the Certificate: Use browser tools or command-line utilities to examine the certificate details. Look for issues such as:
- Validity period
- Issuer and subject names
- Certificate policies
- AIA and CDP URLs
-
Verify the Certificate Chain: Ensure that the certificate chain is complete and valid. Check for missing intermediate certificates and ensure that all certificates in the chain are trusted.
-
Check Revocation Status: Verify the revocation status of the certificate using CRLs or OCSP. Ensure that the system can access the CRLs or OCSP responders specified in the certificate.
4.4. Troubleshooting Steps
Based on the diagnostic findings, implement the following troubleshooting steps:
- Install Missing Intermediate Certificates: If the certificate chain is incomplete, install the missing intermediate certificates. These can typically be obtained from the issuing CA’s website or from the AIA URL specified in the certificate.
- Update Trusted Root Certificates: Ensure that the Trusted Root Certification Authorities store is up-to-date. Windows automatically updates this store through Windows Update, but you can also manually update it using the
certutilcommand. - Disable OCSP Stapling: In some cases, OCSP stapling can cause certificate verification issues. Try disabling OCSP stapling in the browser or application settings.
- Clear SSL State: Clearing the SSL state in the browser can resolve cached certificate issues. This can be done through the browser’s settings.
- Disable Certificate Revocation Checking: As a temporary workaround, you can disable certificate revocation checking. However, this should only be done if you are confident that the certificate is trustworthy.
- Reinstall the Application: If the issue is specific to a particular application, try reinstalling the application. This can resolve corrupted certificate stores or configuration issues.
4.5. Advanced Troubleshooting Techniques
If the above steps do not resolve the issue, consider these advanced troubleshooting techniques:
- Use Network Monitoring Tools: Use network monitoring tools such as Wireshark to capture and analyze network traffic related to certificate verification. This can help identify issues such as blocked CRL/OCSP requests or incorrect certificate chains.
- Examine System Logs: Check system logs for certificate-related errors or warnings. These logs can provide valuable insights into the cause of the issue.
- Contact the Certificate Authority: If you suspect that there is an issue with the certificate itself, contact the issuing CA for assistance.
4.6. Preventing Certificate Verification Issues
To minimize the risk of encountering certificate verification issues, follow these best practices:
- Use Certificates from Trusted CAs: Only use certificates from CAs that are trusted by the operating system or application.
- Keep Certificates Up-to-Date: Renew certificates before they expire.
- Implement Proper Certificate Management Practices: Implement proper certificate management practices, including key generation, storage, and renewal.
- Educate Users: Educate users about the risks associated with untrusted certificates and how to avoid them.
5. The Role of Certificate Transparency in Enhancing Security
Certificate Transparency (CT) is an open framework designed to enhance the security of the SSL/TLS certificate ecosystem. It aims to make the issuance and existence of SSL/TLS certificates more transparent and verifiable, thereby reducing the risk of certificate-based attacks.
5.1. What is Certificate Transparency?
Certificate Transparency (CT) is an initiative that requires Certificate Authorities (CAs) to log all issued SSL/TLS certificates to public, append-only logs. These logs are maintained by independent entities and are publicly auditable.
5.2. How Certificate Transparency Works
The CT framework involves several key components:
- Certificate Authorities (CAs): CAs are responsible for issuing SSL/TLS certificates and logging them to CT logs.
- CT Logs: CT logs are public, append-only logs that store information about issued certificates.
- Monitors: Monitors are entities that continuously audit CT logs for suspicious or unauthorized certificate issuance.
- Auditors: Auditors are entities that verify the integrity and consistency of CT logs.
- Browsers and Applications: Browsers and applications can use CT information to verify the authenticity and validity of SSL/TLS certificates.
When a CA issues a certificate, it submits the certificate to one or more CT logs. The CT log returns a Signed Certificate Timestamp (SCT), which is a proof that the certificate has been logged. The CA then includes the SCT in the certificate or provides it to the website owner.
When a user visits a website, their browser or application can verify the certificate by checking the SCT against the CT logs. If the SCT is valid and the certificate is present in the CT logs, the browser or application can trust the certificate.
5.3. Benefits of Certificate Transparency
Certificate Transparency offers several benefits:
- Detecting Misissued Certificates: CT makes it easier to detect misissued certificates, which are certificates that have been issued without proper authorization.
- Preventing Certificate-Based Attacks: By making certificate issuance more transparent, CT reduces the risk of certificate-based attacks such as man-in-the-middle attacks.
- Improving Trust in the SSL/TLS Ecosystem: CT helps to improve trust in the SSL/TLS ecosystem by providing a mechanism for verifying the authenticity and validity of certificates.
- Promoting Accountability: CT promotes accountability among CAs by making their certificate issuance practices more transparent.
5.4. Adoption of Certificate Transparency
Certificate Transparency has been widely adopted by major CAs, browsers, and operating systems. Google Chrome requires CT for all newly issued certificates, and other browsers are expected to follow suit.
5.5. How to Enable Certificate Transparency
Website owners can enable Certificate Transparency by:
- Requesting SCTs from CAs: When requesting a certificate from a CA, request that the CA include SCTs in the certificate.
- Configuring Web Servers: Configure web servers to serve SCTs to browsers and applications.
- Monitoring CT Logs: Monitor CT logs for unauthorized certificate issuance.
5.6. Challenges of Certificate Transparency
While Certificate Transparency offers significant benefits, it also presents some challenges:
- Log Management: Managing and maintaining CT logs can be complex and resource-intensive.
- Privacy Concerns: CT logs contain information about issued certificates, which may raise privacy concerns.
- Performance Overhead: Verifying SCTs can add some performance overhead to website loading times.
5.7. Future of Certificate Transparency
Certificate Transparency is expected to play an increasingly important role in enhancing the security of the SSL/TLS ecosystem. As adoption of CT grows, it will become more difficult for attackers to use misissued certificates to launch attacks.
6. Staying Ahead of Security Threats: Proactive Certificate Management
Proactive certificate management is essential for maintaining a secure and reliable IT infrastructure. It involves implementing policies and procedures to effectively manage the entire certificate lifecycle, from issuance to renewal and revocation.
6.1. Why Proactive Certificate Management is Important
- Preventing Outages: Expired certificates can cause website outages and application failures. Proactive certificate management helps prevent these outages by ensuring that certificates are renewed before they expire.
- Reducing Security Risks: Misconfigured or unmanaged certificates can create security vulnerabilities. Proactive certificate management helps reduce these risks by ensuring that certificates are properly configured and managed.
- Improving Compliance: Many regulatory standards require organizations to implement proper certificate management practices. Proactive certificate management helps organizations comply with these standards.
- Enhancing Trust: Properly managed certificates enhance trust in the organization’s websites and applications.
6.2. Key Components of Proactive Certificate Management
- Certificate Inventory: Maintain an accurate inventory of all certificates in use, including their expiration dates, issuers, and locations.
- Certificate Monitoring: Monitor certificates for expiration, revocation, and other issues.
- Automated Certificate Renewal: Automate the certificate renewal process to ensure that certificates are renewed before they expire.
- Certificate Revocation: Revoke certificates that have been compromised or are no longer needed.
- Certificate Policy: Establish a clear certificate policy that defines the organization’s requirements for certificate issuance, management, and revocation.
- Certificate Training: Provide training to IT staff on proper certificate management practices.
6.3. Certificate Management Tools
Several certificate management tools are available to help organizations automate and streamline their certificate management processes. These tools can:
- Discover and inventory certificates
- Monitor certificate expiration and revocation status
- Automate certificate renewal
- Manage certificate keys and passwords
- Generate certificate reports
6.4. Best Practices for Proactive Certificate Management
- Establish a Certificate Policy: Develop a comprehensive certificate policy that outlines the organization’s requirements for certificate issuance, management, and revocation.
- Automate Certificate Management Tasks: Automate certificate management tasks such as certificate renewal and revocation to reduce the risk of human error.
- Use a Certificate Management Tool: Use a certificate management tool to automate and streamline the certificate management process.
- Monitor Certificates Regularly: Monitor certificates regularly for expiration, revocation, and other issues.
- Train IT Staff: Provide training to IT staff on proper certificate management practices.
- Test Disaster Recovery Plans: Test disaster recovery plans to ensure that certificates can be restored in the event of a disaster.
6.5. Benefits of Automation
Automating certificate management tasks can offer several benefits:
- Reduced Risk of Outages: Automated certificate renewal helps prevent website outages caused by expired certificates.
- Improved Security: Automated certificate revocation helps reduce security risks associated with compromised certificates.
- Increased Efficiency: Automated certificate management tasks free up IT staff to focus on other tasks.
- Reduced Costs: Automated certificate management can reduce costs associated with manual certificate management.
6.6. Certificate Lifecycle Management
Effective certificate lifecycle management is crucial for maintaining a secure and reliable IT infrastructure. The certificate lifecycle includes the following stages:
- Planning: Determine the organization’s certificate needs and develop a certificate policy.
- Requesting: Request certificates from a trusted CA.
- Issuance: The CA issues the certificates.
- Installation: Install the certificates on the appropriate servers and devices.
- Monitoring: Monitor the certificates for expiration, revocation, and other issues.
- Renewal: Renew the certificates before they expire.
- Revocation: Revoke the certificates that have been compromised or are no longer needed.
- Archiving: Archive the certificates for audit and compliance purposes.
7. Future Trends in Certificate Verification and Management
The field of certificate verification and management is constantly evolving to address emerging security threats and technological advancements. This section explores some of the future trends in this area.
7.1. Increased Automation
Automation is expected to play an even greater role in certificate verification and management in the future. Automated tools will be used to:
- Discover and inventory certificates
- Monitor certificate expiration and revocation status
- Automate certificate renewal
- Manage certificate keys and passwords
- Generate certificate reports
7.2. Enhanced Security
Security will continue to be a top priority in certificate verification and management. Future trends include:
- Stronger Cryptographic Algorithms: The use of stronger cryptographic algorithms such as SHA-3 and post-quantum cryptography.
- Improved Key Management: The use of hardware security modules (HSMs) and other secure key management technologies.
- Increased Use of Certificate Transparency: Widespread adoption of Certificate Transparency to detect misissued certificates.
- Enhanced Revocation Mechanisms: The development of more efficient and reliable certificate revocation mechanisms.
7.3. Cloud-Based Certificate Management
Cloud-based certificate management solutions are becoming increasingly popular. These solutions offer several benefits:
- Scalability: Cloud-based solutions can easily scale to meet the needs of organizations of all sizes.
- Accessibility: Cloud-based solutions can be accessed from anywhere with an internet connection.
- Cost-Effectiveness: Cloud-based solutions can be more cost-effective than on-premises solutions.
7.4. Decentralized Certificate Authorities
Decentralized certificate authorities (DCAs) are emerging as an alternative to traditional CAs. DCAs use blockchain technology to issue and manage certificates in a decentralized and transparent manner.
7.5. Machine Learning and Artificial Intelligence
Machine learning and artificial intelligence (AI) are being used to improve certificate verification and management. These technologies can be used to:
- Detect anomalies in certificate issuance
- Identify potential security threats
- Automate certificate management tasks
7.6. Biometric Authentication
Biometric authentication is being used to secure certificate keys and passwords. Biometric authentication methods include fingerprint scanning, facial recognition, and voice recognition.
7.7. Post-Quantum Cryptography
Post-quantum cryptography (PQC) is a new generation of cryptographic algorithms that are designed to resist attacks from quantum computers. As quantum computers become more powerful, PQC will become increasingly important for securing certificate verification and management.
COMPARE.EDU.VN is your go-to resource for detailed comparisons. For further reading and to explore a multitude of comparisons to aid your decision-making, visit COMPARE.EDU.VN today. Making the right choice has never been easier.
Address: 333 Comparison Plaza, Choice City, CA 90210, United States. Whatsapp: +1 (626) 555-9090. Trang web: COMPARE.EDU.VN
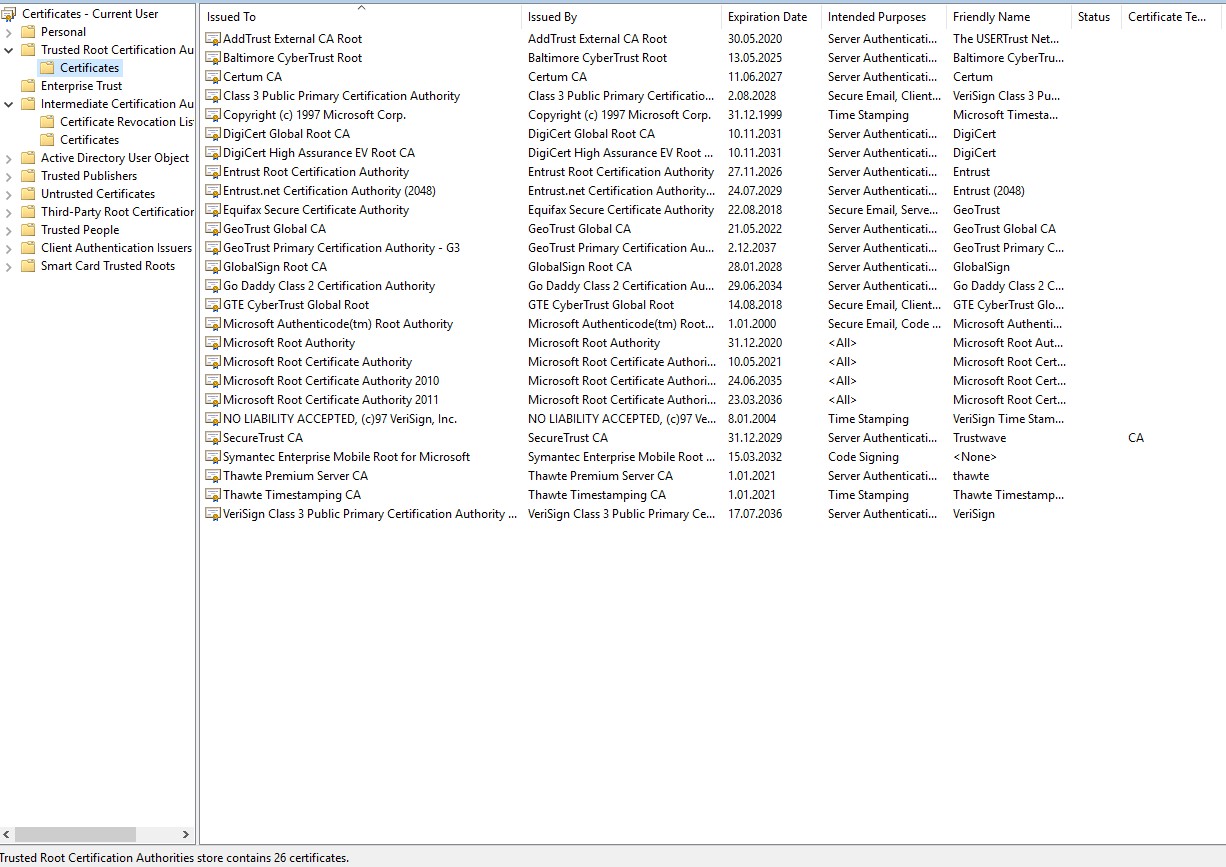 Trusted Root Certificates
Trusted Root Certificates
8. Frequently Asked Questions (FAQ)
8.1. What is a digital certificate?
A digital certificate is an electronic document used to verify the identity of an individual, organization, or device. It is issued by a Certificate Authority (CA) and contains information such as the subject’s name, public key, and the CA’s digital signature.
8.2. Why are digital certificates important?
Digital certificates are important for establishing trust and security in online communications. They are used to encrypt data, authenticate users, and verify the integrity of software.
8.3. What is a Certificate Authority (CA)?
A Certificate Authority (CA) is a trusted organization that issues and manages digital certificates. CAs verify the identity of certificate applicants and ensure that certificates are issued and used in accordance with industry standards.
8.4. What is SSL/TLS?
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are cryptographic protocols used to encrypt communication between a web server and a web browser. Digital certificates are used to authenticate the server and establish a secure connection.
8.5. What is certificate revocation?
Certificate revocation is the process of invalidating a digital certificate before its expiration date. This is done when a certificate has been compromised or is no longer needed.
8.6. What is Certificate Transparency (CT)?
Certificate Transparency (CT) is an open framework designed to enhance the security of the SSL/TLS certificate ecosystem. It requires Certificate Authorities (CAs) to log all issued SSL/TLS certificates to public, append-only logs.
8.7. How can I check the validity of a digital certificate?
You can check the validity of a digital certificate by examining its details in your web browser or using command-line tools such as certutil or OpenSSL.
8.8. What are common certificate verification errors?
Common certificate verification errors include “The certificate is not trusted,” “The certificate has been revoked,” and “The certificate has expired.”
8.9. How can I troubleshoot certificate verification issues?
You can troubleshoot certificate verification issues by checking the system’s date and time, verifying network connectivity, examining the certificate details, and checking the revocation status.
8.10. What is proactive certificate management?
Proactive certificate management involves implementing policies and procedures to effectively manage the entire certificate lifecycle, from issuance to renewal and revocation. It helps prevent outages, reduce security risks, and improve compliance.
Remember, COMPARE.EDU.VN is always here to provide you with comprehensive comparisons to simplify your decision-making process. Whether you’re comparing products, services, or ideas, visit COMPARE.EDU.VN for the information you need to make informed choices.
Address: 333 Comparison Plaza, Choice City, CA 90210, United States. Whatsapp: +1 (626) 555-9090. Trang web: compare.edu.vn