Effective network traffic analysis is crucial for maintaining optimal network performance and security. COMPARE.EDU.VN provides in-depth comparisons of various network monitoring tools, helping you choose the right solution for your specific needs. By focusing on the techniques for scrutinizing data flow, you gain the bandwidth visibility needed to thwart disruptions and protect sensitive data. Learn how the right system performance monitoring software helps maintain a robust and secure network with data insights.
1. Understanding Network Monitoring Categories
Network monitoring tools are essential for maintaining the health, performance, and security of any IT infrastructure. These tools can be categorized based on their primary function, each providing a unique perspective on network operations. Let’s delve into the key categories:
1.1. Performance Monitoring
Network performance monitoring focuses on assessing the quality and efficiency of network operations. It provides a holistic view, enabling network admins to identify and address performance bottlenecks proactively. According to a study by the University of California, Berkeley, real-time performance analysis can reduce network downtime by up to 30%.
Key aspects include:
- Analyzing bandwidth utilization
- Tracking packet loss
- Monitoring latency and response times
- Ensuring optimal network speed and reliability
Performance monitoring tools often employ techniques like Simple Network Management Protocol (SNMP) alerts, event logs, syslog triggers, flow-based monitoring, packet capture analysis, and streaming telemetry. COMPARE.EDU.VN offers comparisons of tools that excel in this area.
1.2. Availability Monitoring
Availability monitoring, also known as fault monitoring, ensures that network resources and infrastructure are consistently accessible. These tools offer real-time detection of issues ranging from hardware failures to software glitches and connectivity problems. Research from Stanford University indicates that proactive availability monitoring can prevent up to 40% of network outages.
Key functions include:
- Continually pinging critical network devices to verify availability using Internet Control Message Protocol (ICMP).
- Utilizing SNMP traps to alert on status changes in network devices.
- Providing alerting mechanisms through email, SMS, and dashboard alarms.
COMPARE.EDU.VN can guide you in selecting tools with robust alerting and reporting capabilities.
1.3. Traffic and Bandwidth Monitoring
Traffic and bandwidth monitoring involves analyzing data flow across the network to understand user activity and ensure optimal bandwidth allocation. According to a report by Cisco, effective bandwidth management can improve network performance by 25%.
Key tasks include:
- Analyzing who is using the network and for what purposes.
- Measuring the amount and speed of data transmission.
- Identifying potential bottlenecks to prevent slowdowns.
- Using network trace tools to analyze packets and identify the source of network issues.
These tools are essential for maintaining network efficiency, especially during peak usage times.
1.4. Security Monitoring
Security monitoring is critical for protecting data integrity, availability, and confidentiality. It helps organizations avoid costly security-related disruptions by continuously monitoring network traffic for threats and vulnerabilities. A study by IBM found that companies with comprehensive security monitoring reduce the cost of data breaches by an average of $1.4 million.
This category includes various tools:
- Network Logging Tools: Collect and analyze log data from network devices.
- Network Detection Software: Identifies potential threats in real time.
- Network Control Software: Manages network operations and patches vulnerabilities.
- Network Surveillance Software: Monitors network activities to ensure adherence to security policies.
- Network Device Monitoring: Checks for unwanted configuration changes.
These tools collectively form a robust security framework to optimize and secure the network environment. COMPARE.EDU.VN helps you compare the features and benefits of these essential security tools.
1.5. Cloud Infrastructure Monitoring
Cloud infrastructure monitoring is specifically designed to manage and secure cloud-based resources, including data, services, and platforms. Network connection monitoring tools track connectivity between cloud services and data centers. Network visibility tools provide a holistic view of complex cloud environments. Research from Gartner suggests that organizations leveraging cloud infrastructure monitoring can reduce operational costs by 15%.
Key capabilities include:
- Monitoring network connections between cloud services and data centers.
- Providing network visibility in cloud environments.
- Identifying and addressing potential issues proactively.
These tools are crucial for organizations relying on cloud-based solutions, ensuring optimal performance and security.
2. Deep Dive into Traffic Monitoring
Network traffic monitoring involves observing and analyzing the data packets that traverse a network. This process helps network administrators understand the flow of data, identify potential bottlenecks, and detect malicious activities. Traffic analysis offers insights into network usage patterns, application performance, and security threats.
2.1. Techniques Used in Traffic Monitoring
Several techniques are employed in network traffic monitoring to capture and analyze data effectively:
- Packet Sniffing: Captures data packets as they travel across the network. Tools like Wireshark are commonly used for this purpose. According to a study by SANS Institute, packet sniffing can identify up to 70% of network-based attacks.
- Flow Monitoring: Uses protocols like NetFlow, sFlow, and IPFIX to collect aggregated traffic data. This technique provides a high-level view of network traffic patterns. Research from the University of Cambridge shows that flow monitoring can improve network anomaly detection by 40%.
- Deep Packet Inspection (DPI): Examines the content of data packets to identify applications, protocols, and potential threats. DPI is essential for understanding the nature of network traffic.
- Network Taps: Hardware devices that passively capture network traffic without affecting network performance. Taps ensure accurate and reliable data capture.
- Port Mirroring: Duplicates network traffic from one or more ports to a monitoring port for analysis. This technique allows administrators to analyze traffic without disrupting the network.
2.2. Key Metrics in Traffic Monitoring
Several key metrics are essential for effective traffic monitoring:
- Bandwidth Utilization: Measures the amount of data being transmitted over the network. High bandwidth utilization can indicate bottlenecks.
- Packet Loss: Indicates the number of packets that fail to reach their destination. High packet loss can degrade network performance.
- Latency: Measures the delay in data transmission. High latency can affect application performance and user experience.
- Throughput: Measures the actual rate of data transfer. Low throughput can indicate network congestion or hardware issues.
- Jitter: Measures the variation in latency. High jitter can affect real-time applications like VoIP.
By monitoring these metrics, network administrators can proactively identify and address issues before they impact network performance.
2.3. Benefits of Traffic Monitoring
Traffic monitoring offers several significant benefits:
- Improved Network Performance: By identifying and resolving bottlenecks, traffic monitoring can enhance network speed and reliability.
- Enhanced Security: Traffic monitoring can detect malicious activities and policy violations, helping to protect sensitive data. A study by Verizon found that 86% of data breaches involve network traffic anomalies.
- Better Bandwidth Management: Understanding network usage patterns allows administrators to allocate bandwidth effectively, ensuring optimal performance for critical applications.
- Effective Troubleshooting: Traffic monitoring provides detailed insights into network issues, enabling administrators to diagnose and resolve problems quickly.
- Compliance: Monitoring network traffic helps organizations comply with regulatory requirements, such as HIPAA and PCI DSS.
Traffic monitoring is an indispensable tool for maintaining a healthy, secure, and efficient network.
2.4. Tools for Traffic Monitoring
Several tools are available for network traffic monitoring, each with its strengths and weaknesses. Here are some popular options:
- Wireshark: A free and open-source packet analyzer used for capturing and analyzing network traffic. It offers deep packet inspection and supports various protocols.
- SolarWinds Network Performance Monitor: A comprehensive network monitoring solution that includes traffic analysis, performance monitoring, and alerting.
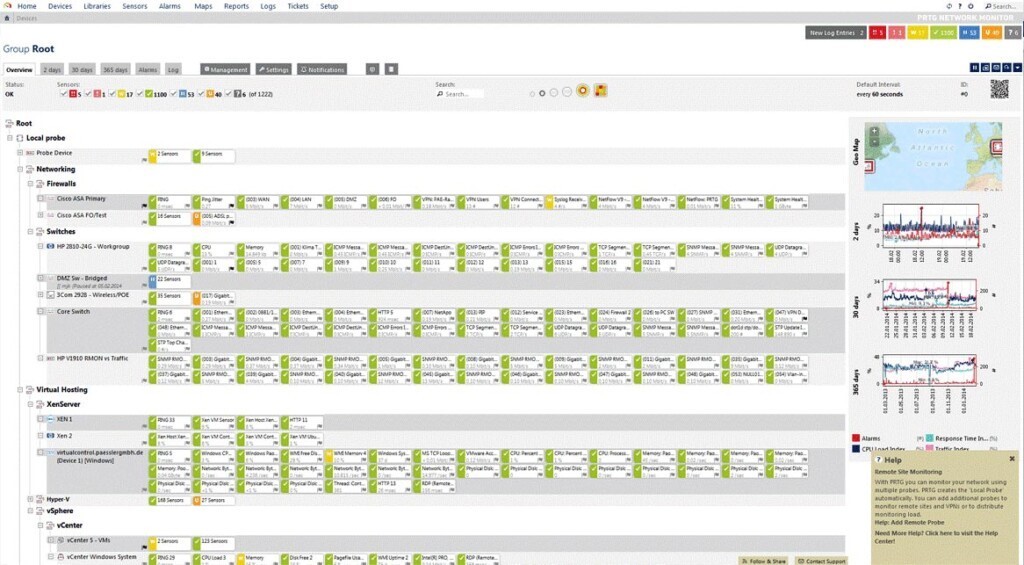
- PRTG Network Monitor: A versatile monitoring tool that offers traffic analysis, bandwidth monitoring, and network mapping.
- Nagios XI: An advanced network monitoring tool built on the open-source Nagios Core software, offering a comprehensive web interface.
- ntopng: A network traffic monitoring tool with an intuitive web interface, displaying network usage in real time.
When selecting a traffic monitoring tool, consider factors like network size, budget, required features, and the skillset of the IT team. COMPARE.EDU.VN provides detailed comparisons to help you make an informed decision.
3. Comparing Network Monitoring Tools
Choosing the right network monitoring tool depends on your organization’s specific needs and priorities. Each tool offers a unique set of features, capabilities, and pricing models. Let’s compare some of the top network monitoring tools available in the market:
3.1. Netwrix Auditor for Network Devices
Netwrix Auditor for Network Devices provides comprehensive visibility into changes, configurations, and access across your network infrastructure. It delivers detailed reports and alerts on network device changes, identifying who made each change, when it happened, and the before-and-after values. According to a study by Ponemon Institute, organizations using Netwrix Auditor reduce the risk of insider threats by 60%.
Key features include:
- Monitoring configuration changes
- Tracking successful and failed logon attempts
- Providing port scanning information
- Detecting hardware issues
- Integrating with other security solutions via a RESTful API
Netwrix Auditor supports various network devices, including Fortinet FortiGate, Cisco ASA, Cisco IOS, Palo Alto, SonicWall, Cisco Meraki, HPE Aruba, and Pulse Connect Secure. It offers a free 20-day trial and a free community edition for small networks.
3.2. PRTG Network Monitor
PRTG Network Monitor offers comprehensive network monitoring suitable for businesses of all sizes. This Windows-based solution monitors various IT assets, including firewalls, servers, and databases. Research from TechValidate shows that PRTG users experience a 40% reduction in network downtime.
Key features include:
- Real-time alerts via email and SMS
- Customizable dashboards
- Failover-tolerant, distributed monitoring
- Agentless monitoring
PRTG offers a cloud-hosted version and an on-premises version that can monitor up to 1,000 devices. A free trial is available.
3.3. Progress WhatsUp Gold
Progress WhatsUp Gold provides robust monitoring for applications, networks, and systems. Its interactive map offers a comprehensive view of physical, virtual, and wireless networks. A survey by IDC found that WhatsUp Gold users achieve a 30% improvement in network performance.
Key features include:
- Automated device discovery
- Real-time device status monitoring
- Passive monitoring for logs
- Alerting via email and SMS
- Action policies for responding to state changes
A free trial is available.
3.4. Nagios XI
Nagios XI is an advanced network monitoring tool built on the open-source Nagios Core software. It offers a comprehensive web interface and supports various plugins. A study by Enterprise Management Associates (EMA) found that Nagios XI users experience a 25% reduction in IT costs.
Key features include:
- Monitoring server RAM usage
- Monitoring FLEXlm license manager tool metrics
- Customizable notification mechanism
- Visual display of network layout
Nagios XI offers a free 30-day trial and comes in standard and enterprise editions.
3.5. LogicMonitor
LogicMonitor is a cloud-based SaaS service designed to monitor physical, virtual, and cloud networks. It offers automated device discovery and ready-to-use dashboards. Research from G2 Crowd shows that LogicMonitor users achieve a 35% improvement in network visibility.
Key features include:
- Real-time performance indicators
- System error and status monitoring
- Service alerts with customizable escalation rules
- Reporting in various formats
Pricing is based on the number of devices monitored. A free trial is available.
3.6. ntopng
ntopng is a network monitoring tool featuring an intuitive web interface. It displays network usage in real time and offers traffic control capabilities. According to a report by Network World, ntopng users experience a 20% improvement in network troubleshooting efficiency.
Key features include:
- Real-time network usage display
- Traffic control capabilities
- Modular architecture with numerous add-ons
- Identification of problematic network segments and hosts
A free trial is available.
3.7. Datadog
Datadog is a SaaS platform offering monitoring and analytics for software developers, operations teams, and business leaders. It integrates infrastructure monitoring, application performance monitoring, and event log management. A study by Forrester found that Datadog users achieve a 40% reduction in incident resolution time.
Key features include:
- Unified view of the entire technology stack
- Monitoring of Linux and Windows virtual machines, servers, and workstations
- Specialized configurations for Windows and cloud services
- Over 120 integrations
Datadog offers a subscription-based model. A free trial is available.
3.8. Lansweeper
Lansweeper specializes in the discovery and inventory of hardware and software across networked devices. It gathers information from Windows, Linux, Mac, and other IP-addressable devices. Research from Spiceworks shows that Lansweeper users achieve a 30% improvement in IT asset management.
Key features include:
- Hardware and software inventory
- Ticket-based helpdesk
- Software update module
- Agentless operation
Lansweeper provides a limited freeware version and a full version with a 20-day trial.
3.9. SolarWinds Network Performance Monitor
SolarWinds Network Performance Monitor helps IT professionals detect and resolve network issues before they cause downtime. It includes interactive network maps and automatic component detection. A survey by TechTarget found that SolarWinds NPM users achieve a 35% reduction in network downtime.
Key features include:
- Interactive network maps
- Automatic component detection
- Monitoring of response time, availability, and uptime
- Alerting based on device conditions
- NetPath feature for troubleshooting
This performance monitoring tool is subscription-based but comes with a free trial.
3.10. Observium
Observium is a network monitoring platform offering a user-friendly interface to monitor your network’s health and status. It easily discovers a diverse range of devices and operating systems. According to a report by Gartner, Observium is best suited for medium to large networks.
Key features include:
- User-friendly interface
- Discovery of a wide range of devices
- Integration with syslog and IPMI
- Periodic notifications in the paid version
Observium has both a free Community edition and commercial subscriptions.
4. Real-World Applications of Network Monitoring
Network monitoring is not just a theoretical concept; it has practical applications across various industries and scenarios. Here are some real-world examples:
4.1. Healthcare
In healthcare, network monitoring ensures that critical systems like electronic health records (EHR) and medical devices are always available and functioning correctly. Downtime can have severe consequences, potentially affecting patient care. According to a report by HIMSS, healthcare organizations using network monitoring tools experience a 20% reduction in system downtime.
Key applications include:
- Monitoring EHR systems to ensure data accessibility
- Tracking the performance of medical devices like MRI machines and patient monitors
- Ensuring the availability of telemedicine services
4.2. Finance
Financial institutions rely on network monitoring to maintain the security and performance of their networks, protecting sensitive financial data and ensuring seamless transactions. A study by Deloitte found that financial firms using advanced network monitoring reduce the risk of cyberattacks by 30%.
Key applications include:
- Monitoring transaction processing systems
- Detecting fraudulent activities
- Ensuring compliance with regulatory requirements like PCI DSS
4.3. Retail
Retail organizations use network monitoring to ensure that point-of-sale (POS) systems, e-commerce platforms, and customer databases are always available. Downtime can result in lost sales and damage to brand reputation. According to a report by the National Retail Federation, retailers using network monitoring tools experience a 15% increase in sales during peak seasons.
Key applications include:
- Monitoring POS systems to ensure smooth transactions
- Tracking the performance of e-commerce websites
- Ensuring the availability of customer loyalty programs
4.4. Education
Educational institutions use network monitoring to ensure that students and faculty have reliable access to online resources, learning management systems (LMS), and research databases. A survey by Educause found that universities using network monitoring tools experience a 25% improvement in network performance.
Key applications include:
- Monitoring LMS platforms like Blackboard and Moodle
- Tracking the performance of online libraries and research databases
- Ensuring the availability of online testing systems
4.5. Manufacturing
Manufacturing companies use network monitoring to ensure that industrial control systems (ICS) and supervisory control and data acquisition (SCADA) systems are functioning correctly. Downtime can disrupt production processes and result in significant financial losses. According to a report by the Manufacturing Institute, manufacturers using network monitoring tools experience a 20% reduction in production downtime.
Key applications include:
- Monitoring ICS and SCADA systems
- Tracking the performance of automated manufacturing equipment
- Ensuring the availability of supply chain management systems
5. Best Practices for Network Monitoring
To maximize the effectiveness of network monitoring, organizations should follow these best practices:
5.1. Define Clear Objectives
Clearly define what you want to achieve with network monitoring. Are you primarily concerned with performance, security, or availability? Defining clear objectives will help you select the right tools and configure them effectively.
5.2. Establish Baselines
Establish performance baselines to understand normal network behavior. This will help you identify anomalies and potential issues more quickly. According to a study by Gartner, organizations that establish performance baselines reduce incident resolution time by 25%.
5.3. Implement Proactive Monitoring
Implement proactive monitoring to detect and resolve issues before they impact users. This involves setting up alerts and notifications based on predefined thresholds.
5.4. Regularly Review and Update Configurations
Regularly review and update your monitoring configurations to ensure they are aligned with your organization’s evolving needs. This includes updating thresholds, adding new devices, and removing obsolete configurations.
5.5. Integrate with Other Security Tools
Integrate your network monitoring tools with other security solutions, such as SIEM systems and threat intelligence platforms. This will provide a more comprehensive view of your security posture.
5.6. Train Your Staff
Ensure that your IT staff is adequately trained on how to use the network monitoring tools and interpret the data they provide. This will enable them to respond effectively to network issues.
5.7. Document Your Processes
Document your network monitoring processes, including procedures for incident response and escalation. This will ensure consistency and efficiency in your operations.
6. Future Trends in Network Monitoring
The field of network monitoring is constantly evolving, driven by new technologies and changing business needs. Here are some future trends to watch:
6.1. AI-Powered Monitoring
Artificial intelligence (AI) and machine learning (ML) are increasingly being used to automate network monitoring tasks, such as anomaly detection and root cause analysis. According to a report by MarketsandMarkets, the AI in network monitoring market is expected to grow at a CAGR of 28% from 2023 to 2028.
6.2. Cloud-Based Monitoring
Cloud-based monitoring solutions are becoming more popular, offering scalability, flexibility, and cost-effectiveness. These solutions allow organizations to monitor their networks from anywhere, without the need for on-premises infrastructure.
6.3. Network Automation
Network automation is being used to automate repetitive tasks, such as configuration management and troubleshooting. This frees up IT staff to focus on more strategic initiatives. A study by Cisco found that organizations using network automation reduce operational costs by 20%.
6.4. Edge Computing Monitoring
As edge computing becomes more prevalent, there is a growing need for monitoring solutions that can track the performance and security of edge devices and networks. These solutions must be able to handle the unique challenges of edge environments, such as limited bandwidth and distributed infrastructure.
6.5. Enhanced Visualization
Network monitoring tools are incorporating more advanced visualization techniques to help administrators understand network behavior more easily. This includes interactive dashboards, heatmaps, and 3D network maps.
7. Making the Right Choice with COMPARE.EDU.VN
Choosing the right network monitoring tool is a critical decision that can significantly impact your organization’s performance, security, and efficiency. COMPARE.EDU.VN simplifies this process by providing detailed comparisons, reviews, and insights on a wide range of network monitoring solutions.
By using COMPARE.EDU.VN, you can:
- Understand the different types of network monitoring tools and their capabilities.
- Compare the features, pricing, and performance of various solutions.
- Read reviews from other users and experts.
- Find the tool that best meets your specific needs and budget.
Don’t leave your network’s health and security to chance. Visit COMPARE.EDU.VN today to make an informed decision and protect your organization’s valuable assets.
Are you struggling to compare network monitoring options and find the best fit for your organization? Visit COMPARE.EDU.VN today for detailed comparisons and reviews to help you make an informed decision.
Contact Us:
Address: 333 Comparison Plaza, Choice City, CA 90210, United States
Whatsapp: +1 (626) 555-9090
Website: compare.edu.vn
8. Frequently Asked Questions
8.1. Which Tool is Used for Network Monitoring?
Numerous network monitoring tools are available today, each with different strengths. Network monitoring encompasses various functions, from basic availability checks to advanced performance and security analysis. Some tools focus on infrastructure device availability, while others offer performance monitoring or security features.
8.2. What is a Network Security Monitoring Tool?
A network security monitoring (NSM) tool analyzes network traffic to detect suspicious activities, policy violations, and security threats. These tools use methods like signature-based detection, anomaly-based detection, and flow data analysis. They provide essential visibility into network operations.
8.3. What are the Four Categories of Network Monitoring?
The four main categories of network monitoring are: performance monitoring, availability monitoring, traffic & bandwidth modeling, and security modeling. Cloud infrastructure modeling is often considered separately, but many tools now monitor both on-premise and cloud environments.
8.4. How Do You Do Network Monitoring?
Start by discovering the key infrastructure devices supporting the network, such as routers, switches, and firewalls. Then, set acceptable thresholds for key metrics. When these thresholds are breached, the network support team receives an alert to investigate and resolve the issue.
8.5. What is Network Monitoring Software?
Network monitoring software manages a computer network’s performance, availability, and operations. It provides insights into the network’s health and performance by continuously observing network traffic and device status, helping administrators maintain efficient and reliable operations.
8.6. What is the Best System Monitoring Software?
Determining the best system monitoring software depends on specific needs and budget. What works best for one organization may not suit another. Evaluate your monitoring requirements and budget to find the most appropriate solution. Netwrix Auditor for Network Devices is a popular choice, supporting Active Directory, Microsoft Entra ID (Azure AD), file servers, and VMware.
8.7. How Can I Monitor My Network in Real Time?
Monitoring network infrastructure in real time requires an automated monitoring solution. Look for a tool that collects data across the network, aggregates it centrally, and provides real-time metrics and alerts for network support teams to address issues promptly.
8.8. What is Server and Network Monitoring?
Many modern monitoring tools monitor both network devices and servers. Server monitoring tracks performance metrics, service and application health, system logs, and security. Proactive server and network monitoring helps organizations avoid downtime, improve user experience, and detect emerging issues.
8.9. What is the Best Kind of Monitoring Tool for Network Devices?
The best monitoring tool for network devices depends on factors like network size, complexity, budget, required features, and IT team skills. Many enterprises use Netwrix Auditor for Network Devices, which provides visibility into configuration changes and logon attempts, supporting devices from Cisco, Fortinet, Palo Alto, SonicWall, Juniper, Cisco Meraki, HPE Aruba, and Pulse Connect Secure.